Security and data governance are often treated as the same thing. They aren’t. Security is about preventing unauthorized access. Governance is making it easier for people to find the information they need. One is about prevention, and the other is about inclusion.
IT staff are rarely rewarded for making it easier for people to access what they need, but they are punished for data breaches. As a result, security gets most of IT’s focus, and governance may not even be on their radar. Ignoring either area results in problems. I will cover data governance in the next post.
How to Deploy BI System Security
Cloud-based (SaaS) software has revolutionized how security is deployed and managed. Amazon, Microsoft, and Google know how to secure data. They have expert staff dedicated to the function because data breaches are anathema to their business models. They pay top dollar for security expertise, more than you will. As a result, they get the best people for the job. Embrace cloud security protocols and systems because they are more robust and better managed than you will do alone.
Your company email system should already have a security system that you can use as the model for your BI system security. Step one in developing your BI system security model is understanding what security protocols you are using now. For example, you may use Microsoft Outlook for your email system. In that case, you have a defined security model called Active Directory. Active Directory is a robust starting place for defining your BI security model.
Security is a technical topic, so I’m not going to dive into the details of Active Directory. Still, you must understand how your business information system requirements relate to your current security model. Ask your IT staff (or external consulting partners) how to adapt your security model. Allot time for discussion and planning.
Due to Active Directory’s ubiquity, most business information tools will work well with it. Your cloud database, ELT tools and dashboard tools may provide an additional layer of security on top of Active Directory.
Substantial companies may have many different security platforms. For example, OKTA is a cloud-based service designed to manage security across many platforms. An in-depth discussion about OKTA is outside the scope of this series.
Who Should Have Access to What?
Every BI system requires multiple levels of access:
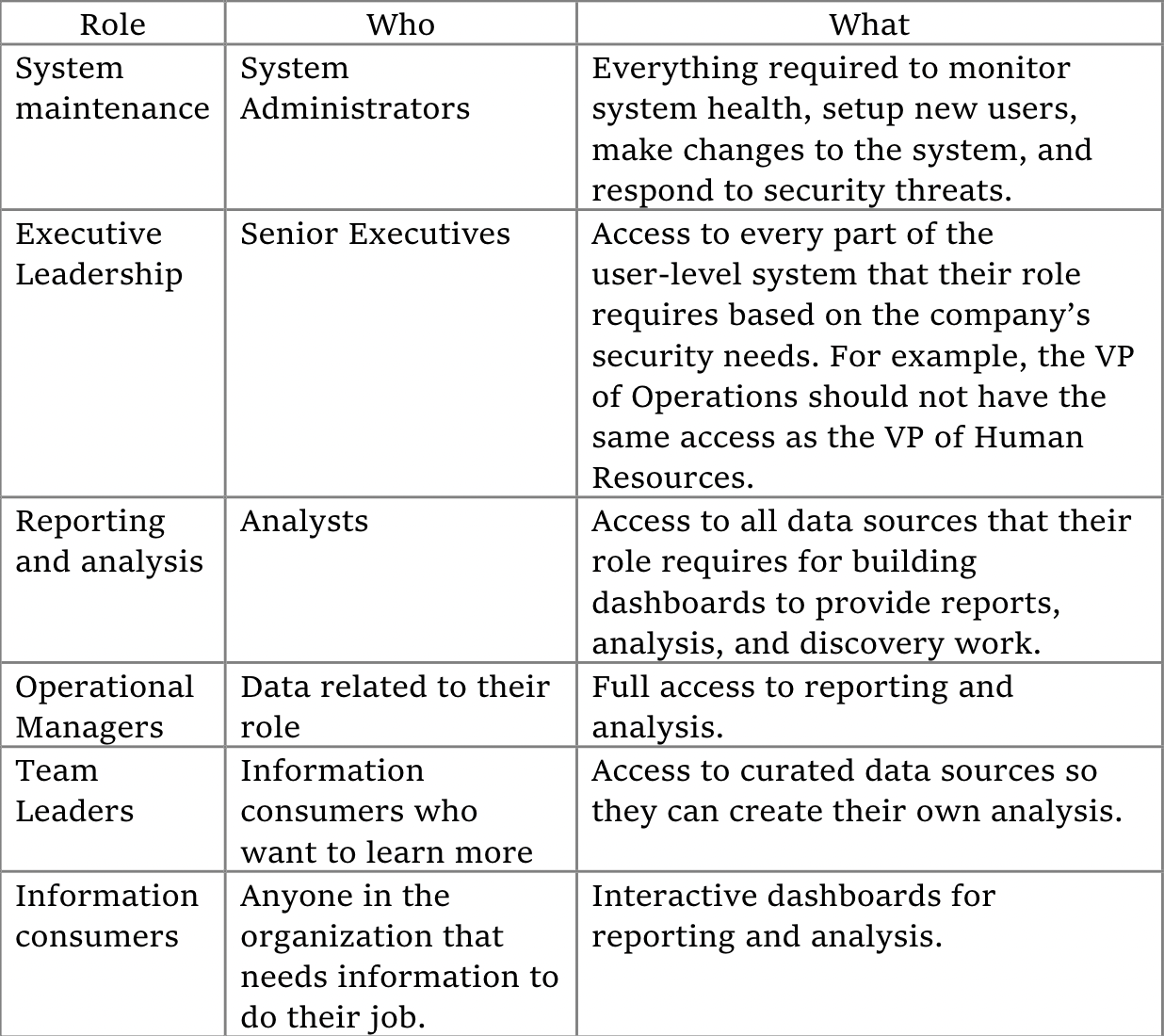
Calibrating data access is unique to every company. Carefully consider the needs of your users when assigning access security. There is a balance. If security is too demanding, you may discourage using the sanctioned data and unwittingly encourage rogue data pipelines.
I’ll discuss how to balance security and data access in my next post on data governance.


