In today’s digital age, mobile devices have become an integral part in everybody’s day to day life. This has allowed users the ability to easily explore and retrieve data visualisations and information via Tableau Mobile.
Several major versions ago, Tableau introduced App Lock, with Biometric or additional passcode security, to ensure data was as protected as it could be, which we will cover first. However, with an advancement in technology comes an equal advancement in risks that we must constantly be looking for and protecting against. This is where Tableau’s new feature, “Additional security policies for Tableau Mobile” comes into use.
App Lock
As mentioned, let’s first cover the initial security in App Lock.
The ability to turn this setting on is achievable via a Site/Server Administrator on both Tableau Cloud and Server via the Settings option on the left panel:
When clicked, let’s head over to the right most option in Mobile to view the specific settings we can work with. Turning on App Lock is as simple as clicking the check box:
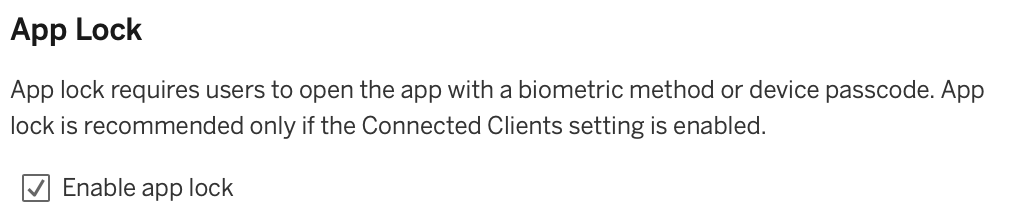
With the box checked, you now have additional levels of security if you have closed the app but, say, left your phone unlocked. This ensures that if a stranger picks up the phone, the data and visualisations on your Tableau Mobile have additional security requirements to access. The ability to add a second app-specific passcode or, for greater security, biometrics such as Face ID or fingerprint on supported devices, ensures that the person accessing the information is authorised to do so.
Offline Previews
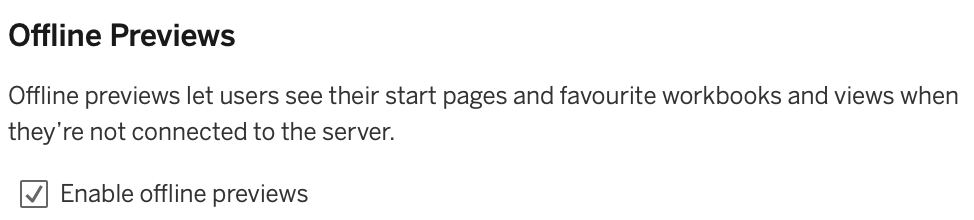
Sometimes we need a balance between security and convenience, as we don’t always have access to the internet on mobiles in signal blackspots, but we may still need access to our data. With a situation like this, the pros need to be weighed against the cons. We can allow users to take snapshots of their favourite workbooks and views to be accessed whilst offline, but could this allow others to see them when they shouldn’t, like if a colleague leaves the company but still has a snapshot of data stored. Whatever your risk management decision is, you have the option to enable Offline Previews with another easy check box:
Mobile Security Policies
Now, let’s look at the new Mobile Security Policies feature and what this means to our end users and admins.
We’re now able to configure security policies on both Android and iOS devices to detect malware, jailbroken/rooted devices, and screenshot or screen record sharing (Android Only).
Note: This is currently not supported on the Mobile Application Managed (MAM) version of Tableau Mobile deployed by business IT departments.
As we investigate each security policy, we will look at the issue and risk its protecting us from.
Jailbreak Detection
Let’s cover what Jailbreaking is shall we?
Jailbreaking or Rooting is a process of removing software restrictions imposed by the manufacturer or service provider on iOS or Android devices, thus allowing users to gain root access to the device’s operating system. This process enables users to install apps, tweaks and extensions that are not available on the official App Store or Play Store.
While jailbreaking can offer some benefits, such as customization and access to additional features, it also poses significant risks to the security of the device and data stored on it. Here are some of the risks associated with jailbreaking:
- Security vulnerabilities: Jailbreaking involves bypassing security measures put in place by the manufacturer, which can leave the device vulnerable to security threats such as malware, spyware and hacking attacks.
- Stability issues: Jailbreaking can cause stability issues and may cause the device to crash or become unresponsive, leading to data loss or other problems.
- Voided warranty: Jailbreaking a device can void the warranty provided by the manufacturer, meaning that any repairs or replacements needed may not be covered.
- Update issues: Jailbroken devices may experience issues when updating to new versions of the operating system, potentially leaving the device open to new security vulnerabilities.
- Compatibility issues: Some apps and features may not work correctly on a jailbroken device, leading to potential issues with functionality or performance.
In conclusion, while jailbreaking may offer some benefits, it poses significant risks to the security and stability of the device.
Malware Detection (Android Only)
Let’s cover what Malware is shall we?
Malware is short for “malicious software,” which is any type of software designed to harm a device, network or system. Malware can be introduced to a device in various ways, such as through phishing emails, software vulnerabilities or downloads from untrusted sources.
Once malware has infected a device, it can cause a range of problems, including stealing sensitive data, damaging files and disrupting normal operations. Some types of malware can also spread to other devices on the network, leading to widespread damage.
One of the most common types of malware is a virus, which is designed to spread and infect as many devices as possible. Other types of malware include spyware, which is designed to monitor a device’s activity and steal sensitive information, and ransomware, which is designed to lock down a device and demand payment to unlock it.
The impact of malware can vary depending on the type and severity of the infection. In some cases, malware may cause minor disruptions, such as slowing down a device or causing pop-up ads. However, in more severe cases, malware can lead to data breaches, financial losses and reputation damage.
Maximum Days Offline Without Policy Refresh
Tableau Mobile will refresh the security policy each time the user opens the app whilst connected to the internet. We know that not every time to user opens the app, they will have internet connectivity, so we are able to provide a grace period of offline time before we perform further steps. We can set this to one or more whole days, and the Server Admin should work with IT and the security teams to agree an acceptable allowance where we ensure we don’t introduce further risk, as an end-user could have jailbroken or downloaded malware prior to reopening the app offline and we want to ensure full protection over our data.
Level of security and enforcement
If Tableau Mobile detects jailbreak, malware or a breach of maximum offline days on the device, we can perform three crucial steps set via the drop-down menu:
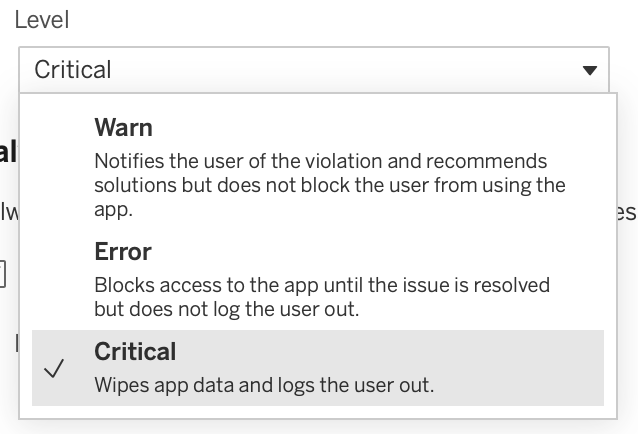
- Warn – Notifies the user of the violation and recommends solutions but does not block the user from using the app.
- Error – Blocks access to the app until the issue is resolved but does not log the user out.
- Critical – Wipes app data and logs the user out.
Prevent Debugging
What is a debugger?
A debugger is a tool that allows a developer to monitor and adapt the code to track and identify bugs within software and applications. By its nature of changing code, debuggers open the risk of injecting malicious code into the application by unauthorised developers. This setting is set by default and can’t be removed due to the risks opened if not present.
Screen Sharing and Screenshots (Android only)
We can probably all agree that screenshotting and screensharing has been an incredible feature introduced to devices that allow us to quickly share pictures, articles and memes to our friends, family and colleagues. With the ability to do this across applications, especially Tableau Mobile, the risk we encounter is the storage and sharing of sensitive information outside of our governed and controlled users. We wouldn’t want a colleague to lose their phone and have hundreds of screenshots of workbooks stored in an unprotected photo album on their device for anyone to see, or the ability to share that data after leaving the business. We are now able to select the check box and block this on Android devices, presenting the end-user with a solid black screen in replacement of the image, thus ensuring greater protection and security over our data.
In conclusion, these new features can ensure the protection of our sensitive data and dashboards whilst mitigating risk of leakage via screenshots or malware. I would encourage any Admins moving to 2023.1 to investigate these features and work with their IT and Security Operations teams to implement them as soon as you upgrade to keep your Cloud and Servers secure. If you have any further questions about this, or have any data work you’d like assistance with, reach out and see what we can do for you.

