Welcome to the final post in our Tableau Bridge series! We started with a simple question of What is Tableau Bridge? We got a bit technical with installation, data source requirements and Pooling, and then created our first schedules. In this last blog, we’ll review how Tableau Bridge secures the transfer of your data in a Windows deployment.
Let’s Get Right to It!
We learned in the third blog that your Bridge client(s) must be installed on a machine behind your firewall to connect Tableau Cloud to your private network data. As such, all communication to and from the Bridge client initiates from behind that private network firewall using ports 80 and 443, and the data transmitted is secured by a TLS 1.2 connection, broadly adopted by devices to authenticate and encrypt data securely.
Knowing that Bridge connects our private network data to Tableau Cloud, let’s breakdown Bridge security at each of these two authentication points.
First, We Must Permit Bridge to Connect to Tableau Cloud.
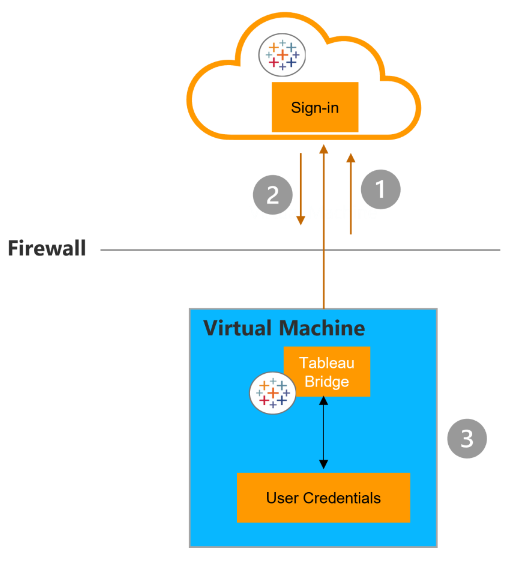
Just as you log in to the Cloud site with your credentials, so too must Bridge connect with a user’s Tableau Cloud credentials (1). Once credentials are passed to Tableau Cloud, an authorization token is returned (2) and the token is stored using Windows credentials manager for use by Bridge to perform various tasks (3):
Next, We Grant Bridge Access to Private Network Data.
This is the section where it helps to have some awareness of the two scheduling types in Bridge (Online vs. Bridge (Legacy)), as the method by which Bridge access this data varies.
For live connections and extracts scheduled for refresh with an Online schedule, database credentials are sent at the time of the request using the TLS 1.2 connection mentioned earlier. These credentials may be embedded during publish time from Tableau Desktop or after publishing to Tableau Cloud from the data source’s Connection tab. If your extract uses a Bridge (Legacy) schedule, those credentials must be entered into the client directly and will be stored in the credentials manager on the computer hosting your Bridge client, to be sent to the database by the client at the scheduled refresh time.
Let’s See These Scenarios in Practice.
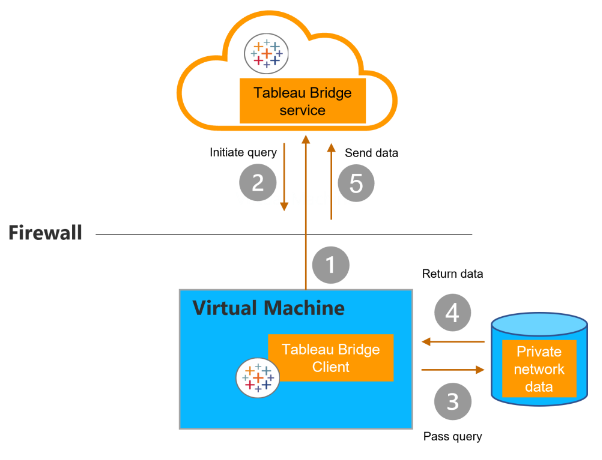
If using a Live or Virtual Connection, we need not consider the schedule type, since there’s no extract to refresh. As such, a persistent connection is established between the Bridge client and Tableau Bridge service using secure WebSockets (1). Pending response from Tableau Cloud (2), the client initiates a live query to the private network data (3). Data is returned (4) and sent to Tableau Cloud (5) via the connection established in step 1:
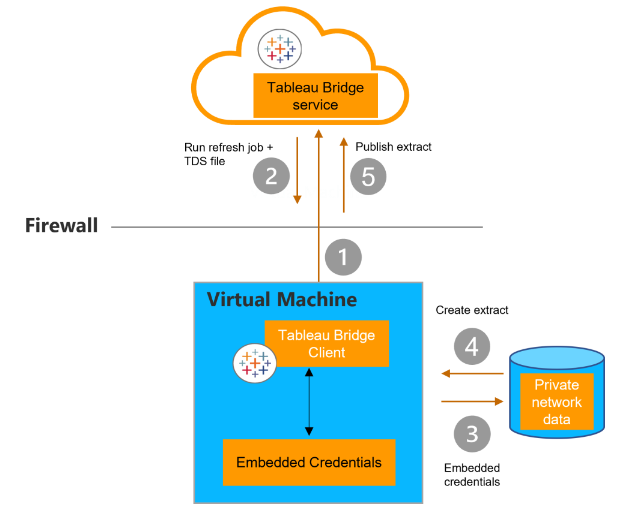
If the data is an extract scheduled for refresh with an Online schedule, a persistent connection is established between the client and Tableau Bridge service using secure WebSockets (1). Pending request from Tableau Cloud, the client contacts Tableau Cloud for the .tds files (2). Using the embedded credentials included in the job request, the client connects to the private network data (3). An extract is created (4) by the client and published to Tableau Cloud using the Bridge service (5).
Although we don’t recommend configuring new refresh extracts with Bridge (Legacy) schedules, we’ll outline the process by which Bridge refreshes extracts of this type.
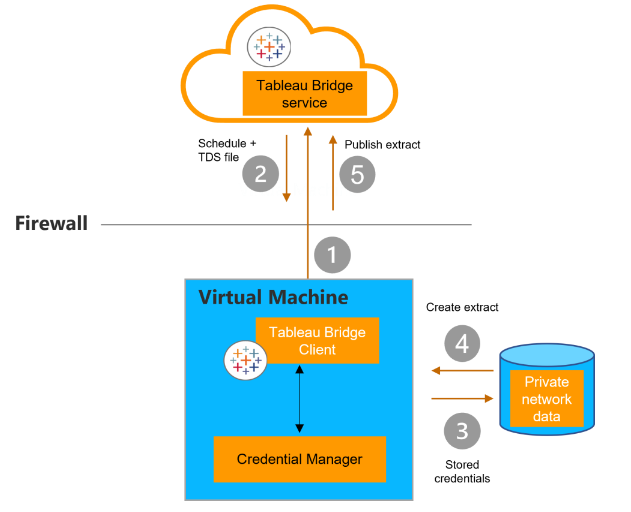
If the data is an extract scheduled for refresh with a Bridge (Legacy) schedule, the Bridge client contacts Tableau Cloud using a secure https connection (1). If available, new refresh schedules and .tds files are sent from Tableau Cloud (2) and a connection is made between the client and the private network data using credentials stored in Windows credential manager (3). The client creates an extract (4) and publishes the extract to Tableau Cloud using Bridge service (5).
While similar in structure, key differences in the procedure to access private network data depend on content and connection type including:
- Live + Extract connections using Online schedules establish a persistent connection from the client to the Bridge service, meaning the network connection remains open after sending a response. Extract connections using Bridge (Legacy) schedules initiate contact with Tableau Cloud, and the channel closes after the exchange.
- Extract connections with Online schedules pass Embedded credentials from the refresh job request, whereas Extract connections with Bridge (Legacy) schedules pass stored credentials from the Windows credentials manager on the virtual machine where the Bridge client is installed.
Other Security Considerations
You may opt to implement domain-based filtering for outbound connections from the Bridge client. Although this is not required, it will ensure that your data is sent to Tableau Cloud only. For a list of domain names required by Bridge for outbound connections, see here.
If you currently have published data sources or workbooks that are connected to private cloud data (e.g., Amazon Redshift, Snowflake, Google BigQuery) and you want to avoid refreshing via Bridge, particularly if you want to connect to these data sources live, Tableau provides the IP address for the host where your site is located. You can then share this information with your IT department to enable Tableau Cloud direct connection to the data.
That’s All for Now!
Achieving data freshness in Tableau Cloud with Bridge requires thoughtful planning and execution, and we hope that this series has empowered you with knowledge to support you and inform this process. If the administrative overhead of maintaining your Tableau Cloud site and Bridge clients still feel daunting, we are here to help. The InterWorks KeepWatch team is dedicated to the cause of supporting your day-to-day Tableau Cloud operations, including Tableau Bridge client management and optimization, so that you can spend your time gleaning data-driven insights from Tableau. Start a conversation by giving us a shout here.
Until next time, thanks for taking this journey with us through all things Tableau Bridge!



