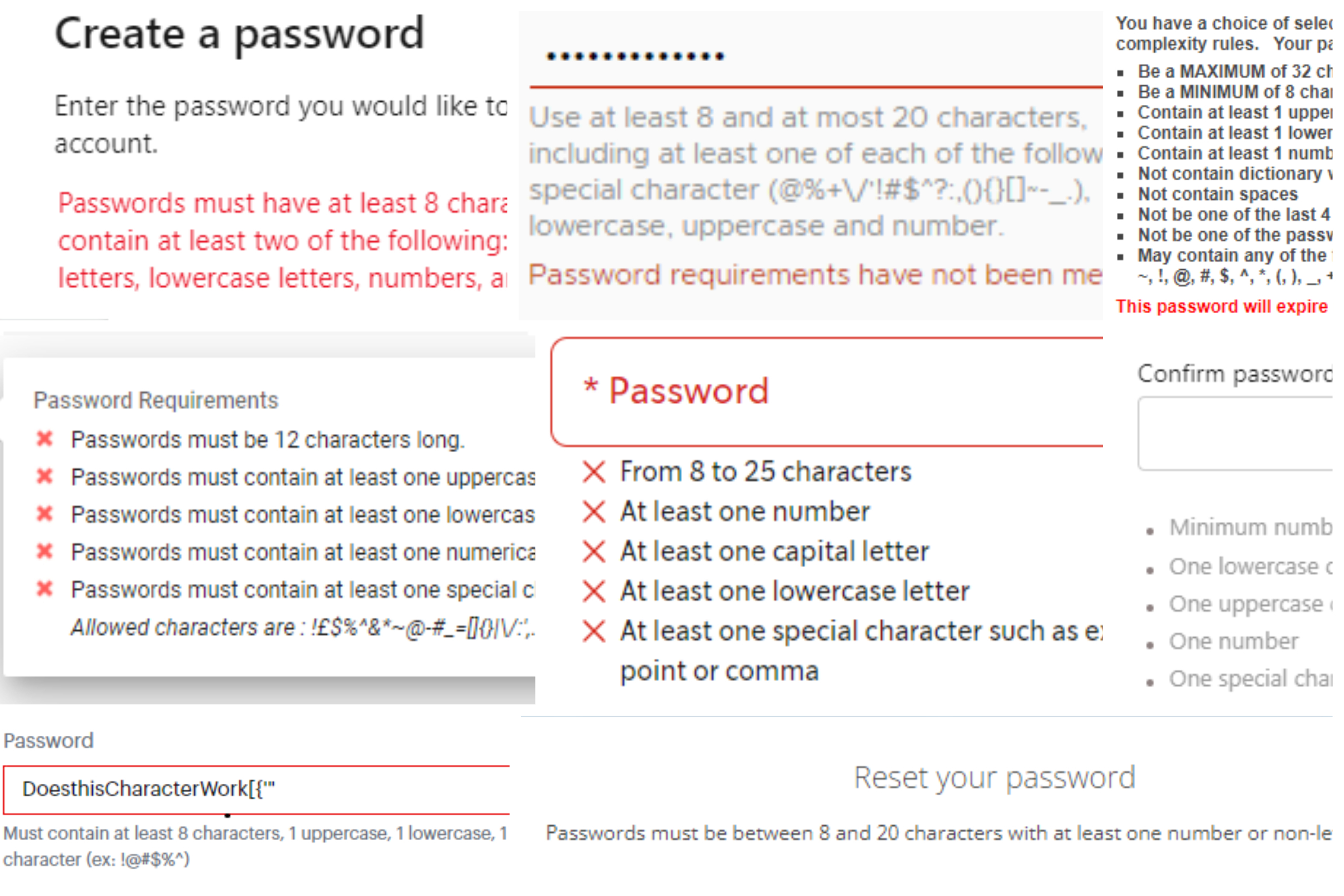
The inspiration for this blog was my seething hatred for overly complex password requirements and a PowerBI report I created to show the math to see if it would help fill my never-ending pit of rage. After discussing the logistics of converting that PowerBI report to a Tableau Dashboard with my buddy Chris Chang from the InterWorks BI team, it started to seem like the topic would be worth bringing to the attention of others through a blog post. In the end I wanted to make sure everyone knew my personal feelings about Password Complexity Vs. Length, and also other steps you can take to keep your accounts secure.
Complexity Vs. Length
The more complex password requirements are, the more likely you are to not remember your password at any given time. At one point in my life, before using password managers, I had accounts where I was resetting my password from email every time I needed to log in. During my tenure as a student at University I probably reset my password 20+ times.
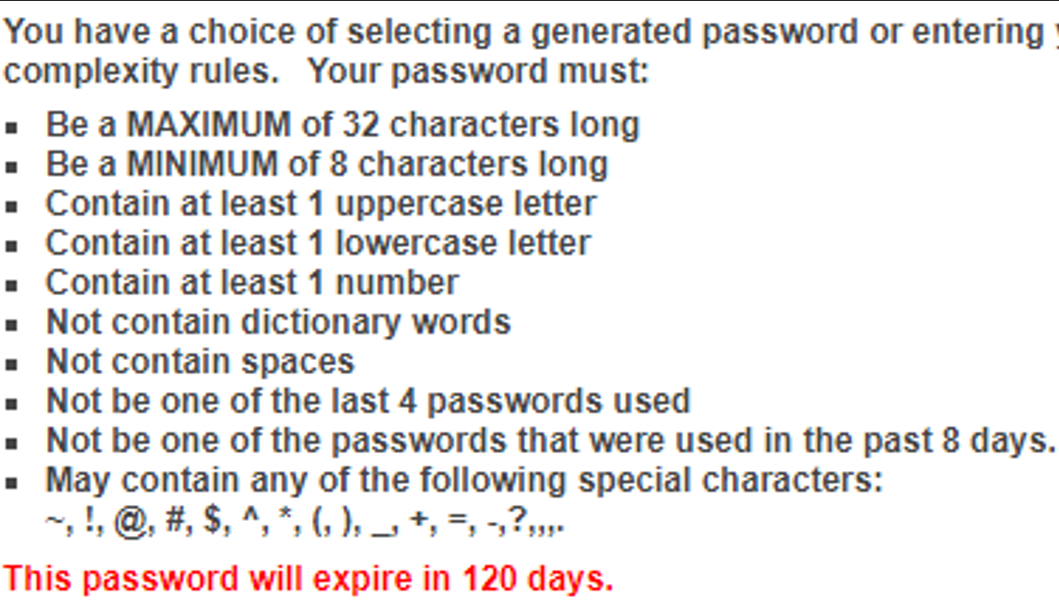
Now there’s a pretty simple way to know how complex/secure your password is, and it’s something everyone loves: MATH! I know everyone wants to do math themselves, but I enjoy taking away other people’s happiness, so please look at the visual below where the math is done for you and adjust it to see different password complexities. (Please note that the following is true for randomly generated passwords, and not relevant for things like dictionary attacks.)
As you can see above, adding special characters to a password does make it more secure than another password of the same length without them, but choosing to instead add an extra characters is even more secure! So, if you want to create a more secure password, length should be your main goal. The best method for a memorable, but lengthy password is doing phrases, such as “IHateSpecialCharacters” or “CollegeWhyDidYouRemoveDictionaryWordsPleaseStop.”
Password Managers
So, as previously mentioned, this only comes into play for truly random passwords. If using the password “Password123,” the complexity isn’t truly 62^11, but something much, much smaller. Then, this circles back to, “If I wanted ultimate security, but also a memorable password, how would I do that?” And the best answer would be password managers.
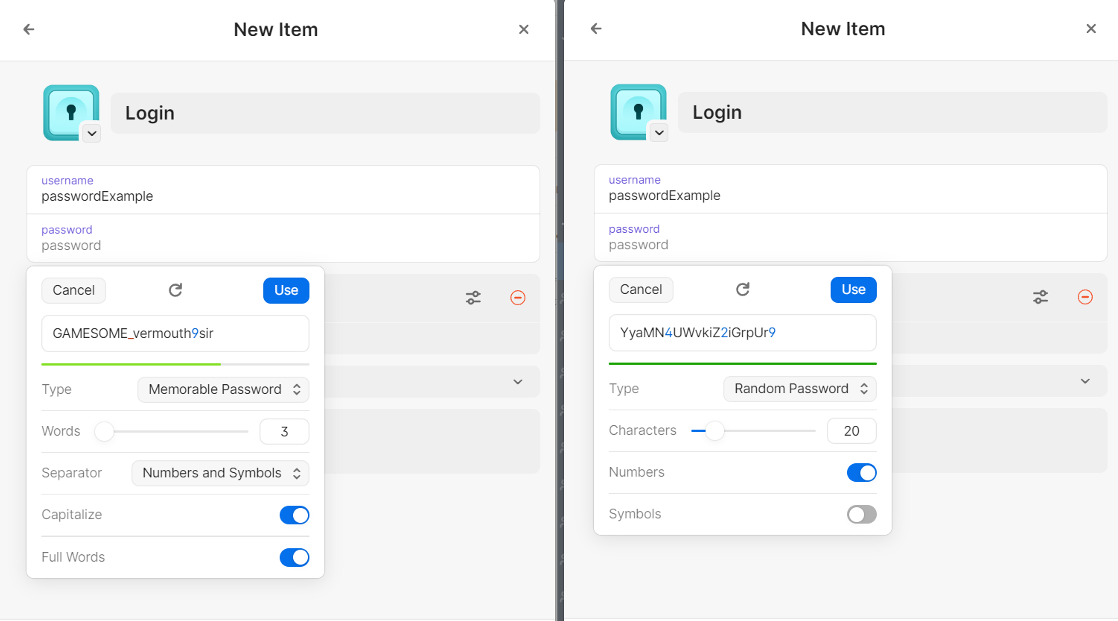
I’ll be totally honest, out of my hundreds of passwords I need as an IT professional who works with clients, I probably have 2-3 of them memorized. The rest come from tools like 1Password, BitWarden, LastPass, etc. where I can generate passwords that are more random, and thus more secure:
MFA
Finally, one of the best ways to secure your accounts is to use MFA whenever it is available. MFA is one of those things you don’t feel like you need until you’ve already been compromised, but hopefully you are able to get it before that point.
You’ve probably heard it a hundred times before, and you’re thinking either, “What are the chances people will target me?” or, “Does MFA really help?” Let me tell you, people are most likely trying your passwords more often than you think. Since enabling MFA of my personally Microsoft account, I have received prompts two different types from someone trying to access my account (Learn from me, don’t reuse passwords, use password managers) which otherwise would have given them full access to my Microsoft account.
We at InterWorks aren’t the only people who believe in the almighty power of the MFA. Gabe Newell, the CEO of Valve (at the time worth $2-$4 billion) trusted his platform’s MFA so much that he gave out his personal username and password to show how secure it was.
Data Breaches
Have you ever found yourself in a Data Breach? A lot of people will say no here, without realizing that
A good way to know is if you visit https://haveibeenpwned.com/ and enter an email address, to see if any data leak has been associated with it, and what that leak maybe have contained.
For example, here is me, having been pwned (through no fault on my own):
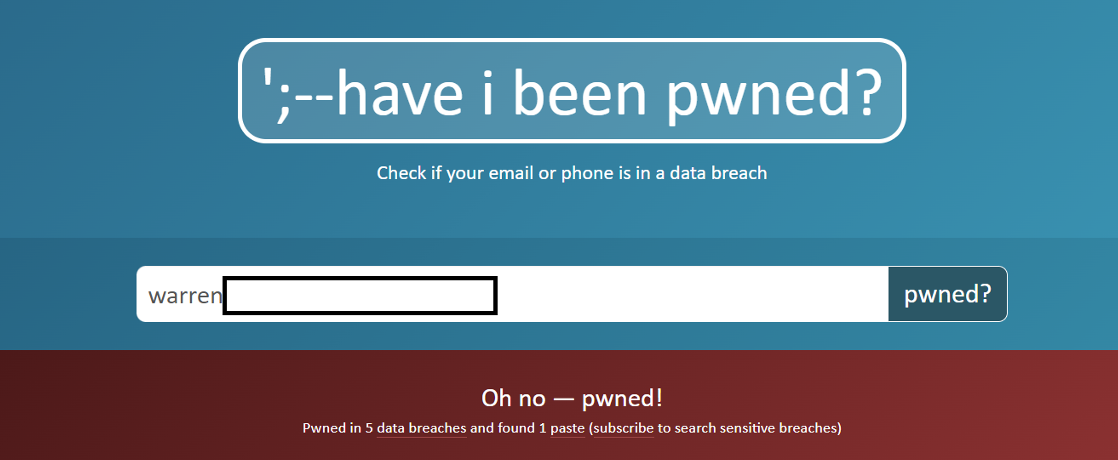
And here is the more specifics for what this breach means for me:
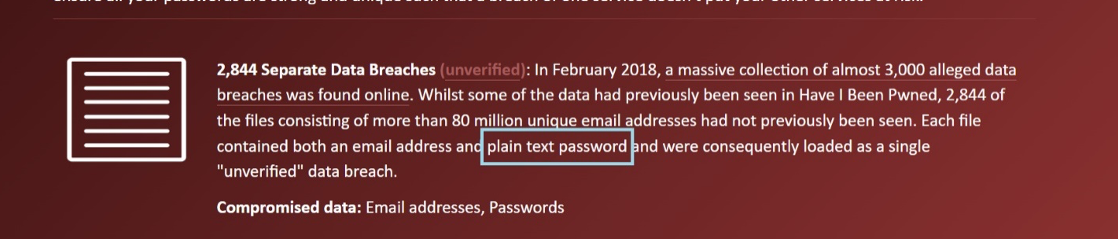
You can see that in these breaches, not only was my email leaked, but so was my unencrypted password. This means everywhere I reused that single password is now vulnerable to being logged into with almost no effort:
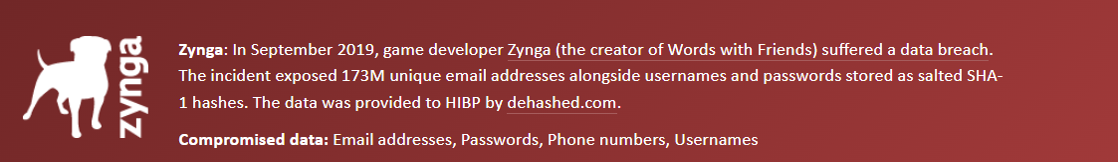
Here, you can see that my password was stolen, but in an encrypted form (SHA-1) so although I am safer than I would be otherwise, it would still be wise to change my password. This is the type of event I am referencing in the Tableau visual above, where we have an encrypted password and we are trying to brute force it.
Conclusion
To summarize, keep an eye on your accounts, and make sure they don’t get compromised. Use tools like HaveIBeenPwned to make sure your email doesn’t show up in anything new. The longer the password is, the longer it’ll take for anyone to be able to break it in a leak (as long as it wasn’t plain text). If you reuse your password, you are opening yourself up for multiple accounts to be compromised if just one is. Password managers make it easier to keep unique passwords for your accounts while remembering just one password. MFA is the little cherry on top, as a last line of defense to prevent unwanted access to an account.
If you want to work with us on your IT needs, feel free to reach out and see what we can do for you!


