Astaro, now part of Sophos Network Security, is a decent security appliance platform that sits atop of iptables for the firewall set. With that, the NAT rules can be a little different. I have experience with many brands, and the Astaro documentation isn’t completely clear on how to set things up.
This is meant to be a simple example of 1-1 NAT with firewall rules. We will expose this public server on a completely different external IP address. There are many supported ways to accomplish this, but here’s one that many parallels can be drawn to.
Server: ServerA
WAN IP: 1.2.3.4 / 32
LAN IP: 192.168.1.15 / 24
First, we need the appliance to advertise that it’s in charge of the new WAN IP.
- Navigate to Interfaces & Routing > Interfaces > Additional Addresses
- Click New additional address…
- Enter the Name, choose the interface, give the IP, and choose the mask. For the mask, use /32 as you are identifying a single host.
- Click Save
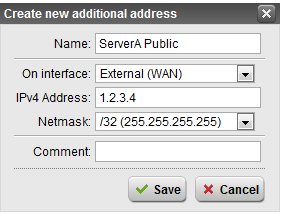
Notice the address by default doesn’t enable, click the green light to toggle the setting on.
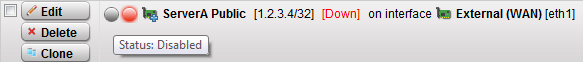
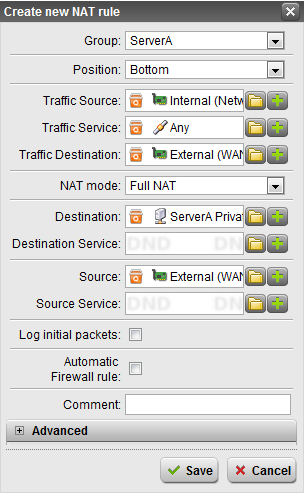
Next, create the inbound NAT rule, the most intuitive one. This is a DNAT or Destination NAT policy.
- Navigate to Network Security > NAT > DNAT / SNAT
- Click New NAT rule…
- Choose the settings as shown below, noting that ServerA Private is an object defined for the Internal interface, and the Public object selected is External (WAN) [Server A Public] (Address).
- Don’t use the automatic firewall rule, it’s lazy, and you can lose track of the holes open, take the time to create a manual firewall rule for the needed services.
- I tend to use groups to keep the NAT rules organized / color coded for easier management. Also, if you have a pre-existing NAT setup, you can easily use the Clone button on the rules.
- Click Save
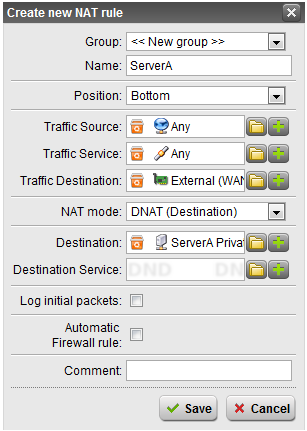
Next, create the outbound NAT rule. This is a SNAT or Source NAT policy.
- Click New NAT rule…
- Choose the settings as shown below. Note that the destination is Internet IPv4, so this only applies when routing to the internet.
- Click Save
Next, if necessary, create a reflexive/loopback NAT policy. This is a Full NAT policy.
- Click New NAT rule…
- Choose the settings as shown below. That is the entire Internal (Network) and the same pubilc object used in the other ruels.
- Click Save
Finally, the rules will show up disabled, click the green light to toggle the three rules to on.
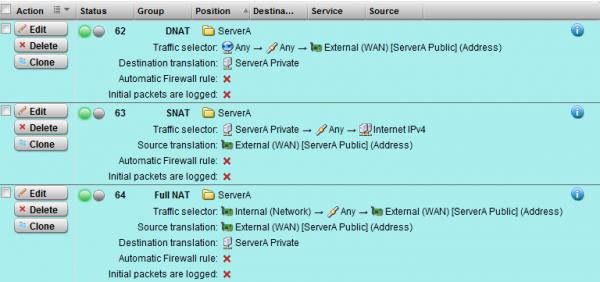
The Full NAT bit is the more confusing one, but satisfies the ability for other users in the 192.168.1.0/24 network to reach ServerA via the public address of 1.2.3.4. This winds up being a loopback operation, and the firewall can’t route traffic from Internal back to Internal without changing the source address. This is quite common, some firewalls or deployments handle this with a different DMZ interface, Proxy ARP, or DNS trickery. There are pros and cons to each solution, and all can be implemented on the Astaro appliances. Be sure to consider the load on the device with the loopback rule as all packets will route in and out of the firewall, where some other methods will be more efficient on the network.
Onto the firewall rules, these are defined under Network Security > Firewall. Some important notes:
Firewall rules are evaluated top down like most other platforms.
A service definition considers the source and destination ports, so HTTP is defined as 1:65535 -> 80, that’s going to be how you have things setup 99% of the time with standard IP communication as the source ports are dynamically assigned per connection.
The destination of an inbound firewall rule uses the private object.
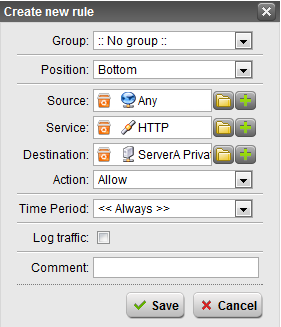
- Click New Rule…
- Configure the settings
- Click Save
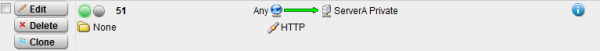
And enable it like before
There you have it; hopefully this helps with the learning curve.

