Overview
Sophos’ Astaro firewall appliances and UTMs can come with a variety of configurable features, such as intrusion prevention, web security, and mail security. Some of these features, such as intrusion prevention, utilize open source technologies, such as Snort (http://www.snort.org/), an open source network intrusion prevention and detection system.
The Problem
After a fairly recent upgrade for a client, it was reported that some downloads were getting dropped. Additionally, it was discovered that the Windows FTP client would time out and could no longer access the client’s public FTP outside the network. The FTP server was showing that a connection was trying to be established; however a connation could not be completed. Oddly enough, 3rd party FTP clients, such as FileZilla, could still access the public FTP.
Identifying the Issue
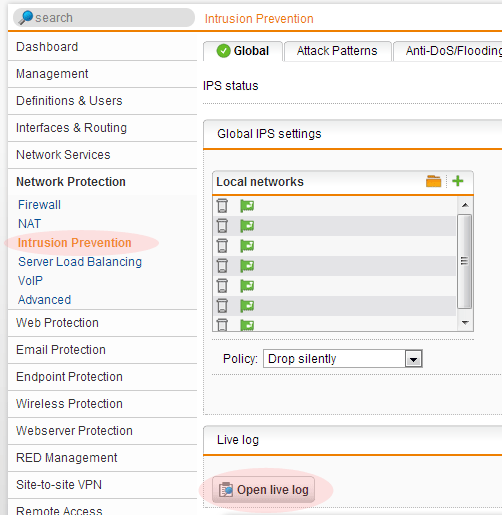
One of the nice things about the Astaro firewall appliance’s/UTM’s is that a live log of a specific feature can be viewed. Since connections were dropping (note in my photo that ‘Drop silently’ is selected), I decided to take a look at the intrusion prevention.
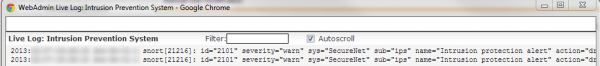
After opening up the logs and I initiated the download again. Since I did not know the IP address of the place I was trying to get my download from (SourceForge in this case), I ran an ipconfig in a command prompt so I would know what information I would need. Here is the code that was returned:
2013:01:09-17:23:13 astarofirewall-01-1 snort[28656]: id="2101" severity="warn" sys="SecureNet" sub="ips" name="Intrusion protection alert" action="drop" reason="FILE-OTHER RealNetworks Netzip Classic zip archive long filename buffer overflow attempt" group="500" srcip="8.8.8.8" dstip="192.168.255.50" proto="6" srcport="80" dstport="51436" sid="24229" class="Attempted User Privilege Gain" priority="1" generator="1" msgid="0"
In my example, there are 3 pieces of information I care about:
- Where I am downloading from, the srcip (source ip): 8.8.8.8.
- Where I’m trying to download to, the dstip (destination ip): 192.168.255.50.
- The sid (Snort rule): 24229
Note: The ‘live log’ will not have syntax highlighting. An example has been provided below.
Adjusting Intrusion Prevention Rules
Before I made adjustments to any rules, I went to Snorts website to research the rule in question. In this particular case, Snort already changed their own default rules on 9/21/2012 http://www.snort.org/vrt/docs/ruleset_changelogs/2_9_3_1/changes-2012-09…
- Step 1: Next, I went to Network Protection > Intrusion Prevention > Advanced
- Step 2: Click on the ‘Plus sign to add the new exception
- Step 3: Add the rule id found from sid.
- Step 4: Check ‘Disable this rule’
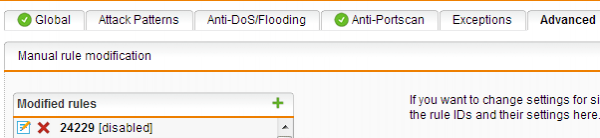
The rule will now appear as disabled in the ‘Modified rules’ list.
Verify that the download is now working correctly.
Note: There are occasions where certain file extension can flag several rules, however may be difficult to flush out as successive rules may not show up in the ‘live log’ until you disable the first rule that is getting flagged.


