Have you ever heard someone say that they never lock their doors? This practice implies that we live in a world where bad people do not exist, that you are not exposing yourself to any risk by doing so, or that nothing bad ever happens around here. Today, this could not be further from the truth, and when it comes to sensitive information, things should not be left out in the open. Let me introduce you to your new friend, Encryption. He’s one of the good guys.
Encryption: “Hi! I’m Encryption.”
You: “Hi there, what is it that you do?”
Encryption: “I protect things from unintended eyes.”
You: “So … like a password?”
Encryption: “Well, sort of, but much more complex than that.”
How complex, you might ask? Well, your average password is likely somewhere between 9-30 characters. 30?! Bravo to you good people; 30 is very strong, and hopefully, there are some creative things stuffed into those 30 characters. But here is the thing: encryption algorithms are much more sophisticated and capable of safeguarding data. Compare 30 characters to the string below:

And this is just a partial snippet of a 4096-bit public key. And that is only half the keys to the kingdom! A file encrypted with this key (in its entirety) would still require a complementary private key to properly decrypt a protected file.
I rest my case.
Cue: PGP Encryption
PGP (Pretty Good Privacy) has been around for 30 years now and is primarily used for sending encrypted emails and encrypting standalone files. Rather than password-protecting a file, which is much easier to crack, by encrypting a file using PGP encryption, you are using a system that involves two very complex keys to safeguard the contents of a file. The public key—which you create and send to someone—is used to change plain-text information within a file into ciphertext that only you can decrypt. Once received, you can then use your private key to decrypt the file and view it as it was originally intended.
For the purposes of this blog article, we will be using two pieces of software in the GPG4win (GNU Privacy Guard for Windows) suite. Did I mention that it’s free?! Download available here.
GnuPG: This is the backend application that does the encrypting/decrypting of files using the PGP protocol.
Kleopatra: This is a handy GUI for the Gpg4win application. It is used to manage keys:
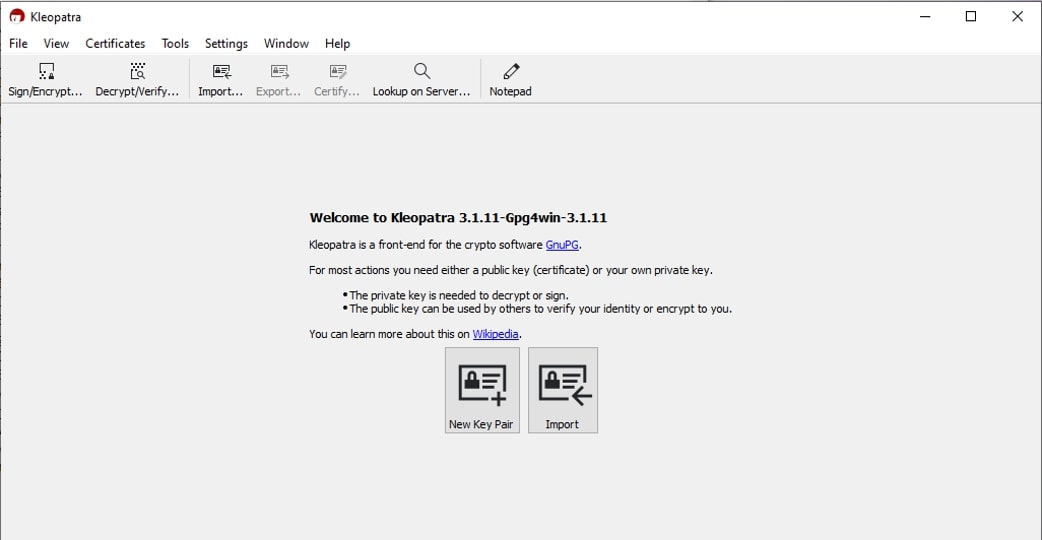
To start storing public keys for other users/recipients, you must first create a key pair for yourself.
Click Open Kleopatra and then the New Key Pair button to begin. Next, input the name and email information. You can also use the Advanced Settings button to define key complexity, key expiration date, etc. Then click Next, then Create:
This is where encryption differs from just a password. Encryption algorithms come in many forms, and depending on the complexity requirements you set (i.e. the number of bits), the harder it is to crack an encryption:
At this point, you should be presented with a popup like this:
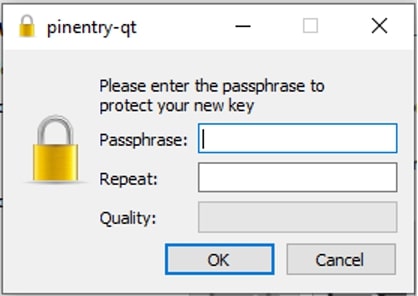
This password is needed to protect your key pair inside the Kleopatra application. Enter your passphrase twice and click OK to finalize your key pair creation. You will be presented with the following screen confirming successful creation:
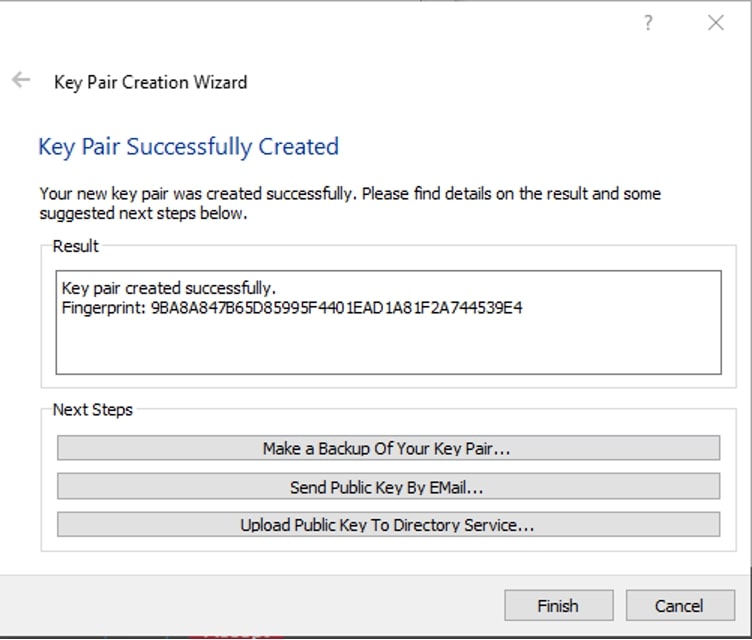
Note: There is an option to back up your key pair. This is a backup of your private key. DO NOT SHARE THIS WITH PEOPLE.
Now you have a personal key pair to use for both encrypting your own files and decrypting files that you have protected or that others have sent to you. But wait, THERE’S MORE!
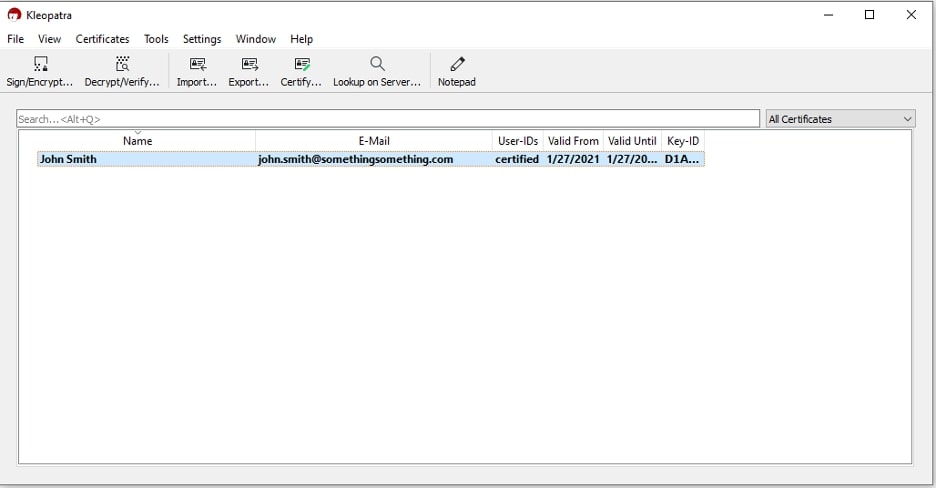
For others to create encrypted files that only you can open, they need to have your public key.
To export your public key, select your name in Kleopatra, click the Export button, and choose a name and location for the file. This will be a .asc file. It might also be helpful to include _public in the file name, so you do not confuse this with your private key.
To add users to your key store, click Import and find the public key they have sent. In this example, I am importing a public key for my friend, aptly named My Friend. Once you have located the file chosen, click Open. You will then be presented with this popup. Click Yes, then Certify:
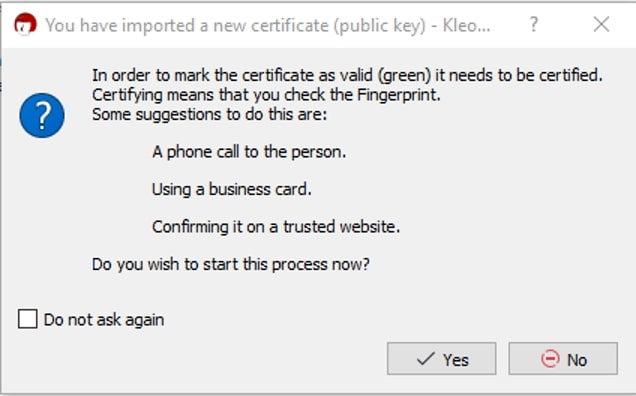
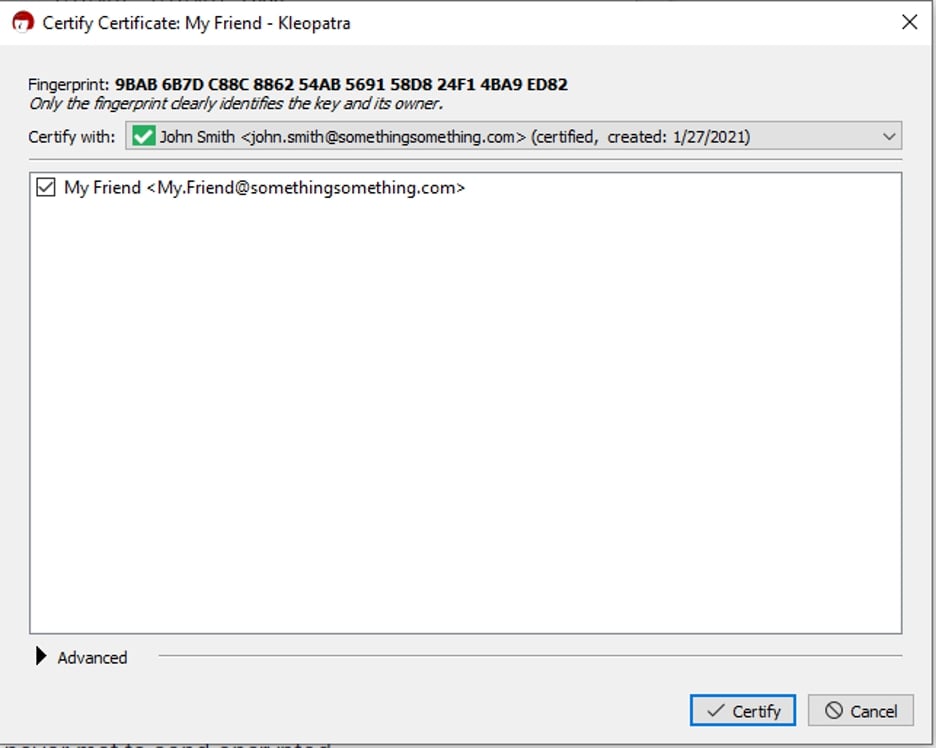
Since you are importing a new key to your personal key store, you will be prompted to enter your passphrase. This is the passphrase you entered twice in the earlier steps above. Click OK:
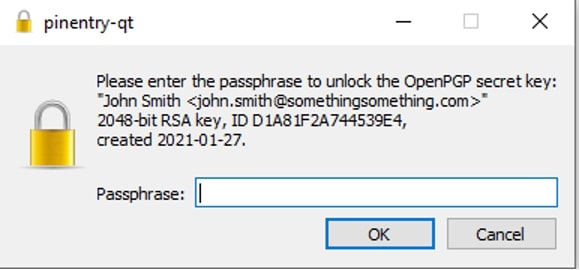
Lock It up! No, You Lock It up!
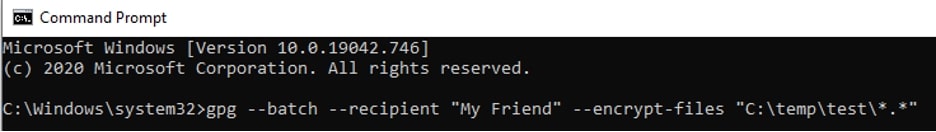
To encrypt a file for My Friend, open Command Prompt and input the following command, substituting your own source file extension and path. The recipient variable should reflect the Name field from within Kleopatra. In this example, I am encrypting all files in my directory, one of which is a text file and the other a spreadsheet.
To Encrypt Files:
gpg --batch --recipient "My Friend" --encrypt-files "C:\temp\test\*.*"
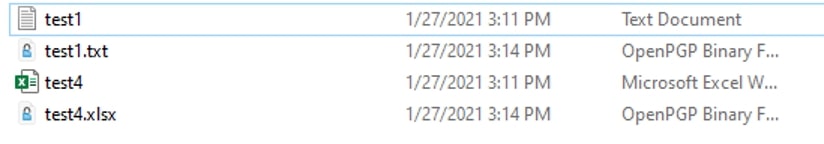
The new .gpg files are created with their prior extension as part of the file name:
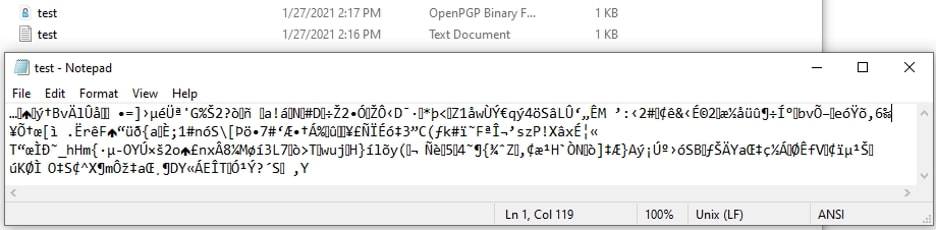
While encryption does not lock an unauthorized user out of a file, it does obscure the information within. When I attempt to open that new encrypted file using a simple text editor, I am only presented with encrypted gibberish. Only the intended recipient possesses the private key which can be used to decode this message:
I Am the Keymaster
Let’s perform that process in reverse. Perhaps you have received a handful of encrypted files from one of your other PGP Pals. They have your public key and have made those files only accessible by you via their PGP application of choice. Open Command Prompt, and enter the following command (again substituting your own file path).
To Decrypt Files:
gpg --batch --recipient "John Smith" --decrypt-files "C:\temp\test\*.gpg"
Your file should now be readable in its proper format:
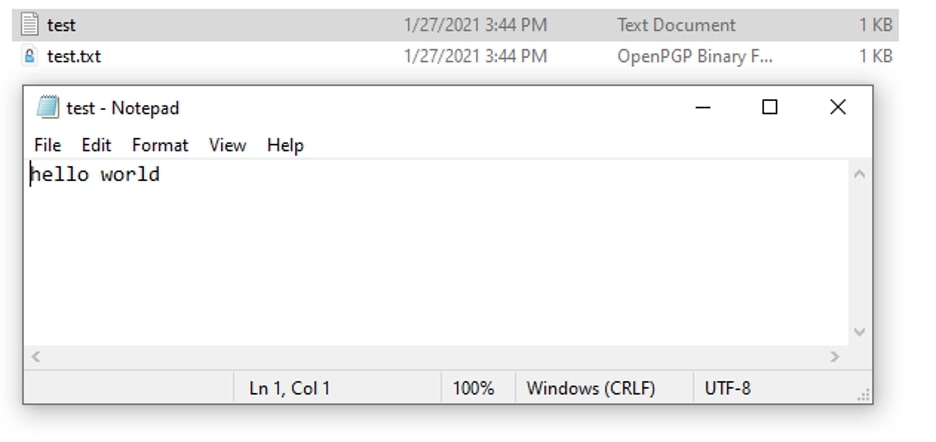
Note: You do not need to keep the Kleopatra application open and running to perform encrypt/decrypt operations. Once you open Kleopatra, it starts the following background process that will continue holding key cache info in memory:
![]()
If the GNuPG key daemon process is ended and Command Prompt exited, the keys will no longer remain in memory. You will need to relaunch Kleopatra. As an alternative, you can create a task in Windows Task Scheduler to start the Daemon process at login using the following action settings:
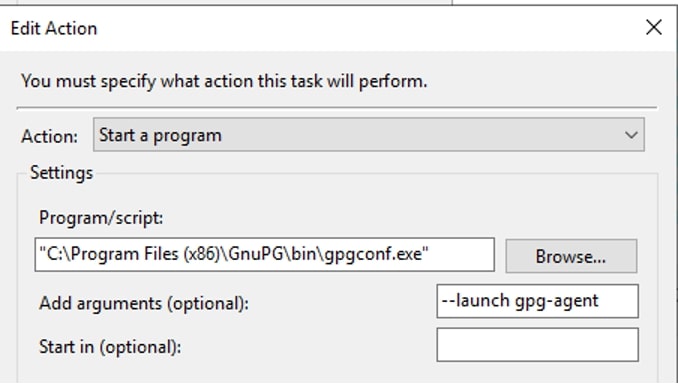
And there you have it! These steps are the beginnings of working with PGP file encryption, but you can certainly get more in depth, setting up scripts to periodically run to either encrypt or decrypt files, depending on your needs.
For additional commands that can be passed to GnuPG, please visit the GnuPG documentation.
Stay safe out there!


