There are various reasons you may wish to access the backend of a Linux virtual machine. In regards to a Matillion server, which is hosted on a Linux operating system, this could be for a variety of reasons, including but not limited to:
- Retrieving historic logs
- Running updates
- Setting up SSH keys for Matillion to leverage when connecting to other platforms
- Working with Matillion Support if there are issues with your Matillion application
Prerequisites
- Administrator credentials to your Linux virtual machine. This could be either:
- A username and password
- A username and private SSH key
- The OpenSSH Client optional service must be enabled on your machine, and OpenSSH must be added to your PATH environment variable. You can read how to do that here.
Logging into a Linux Virtual Machine via SSH
Logging into a Linux Virtual Machine via SSH with a Username and Password
Using the console or command line, use the ssh user@host command to access the server. You will be prompted for your password:
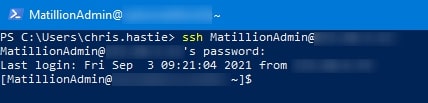
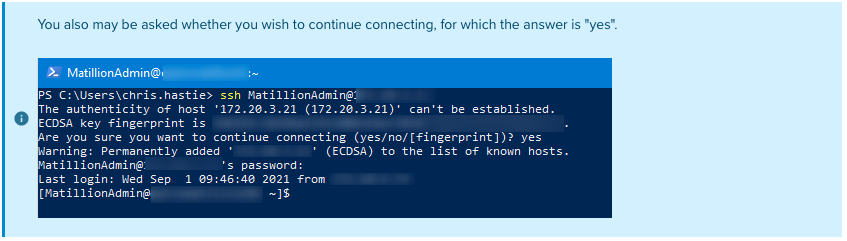
That’s all there is to it really, so short and sweet!
Logging into a Linux Virtual Machine via SSH with a Username and SSH Key
1. Using the console or command line, use the ssh user@host -i path/to/private/key command to access the server. If you log in successfully, skip to the next section. Otherwise, it is likely you were presented with an error stating that your private SSH key is too open, like in the following screenshot:
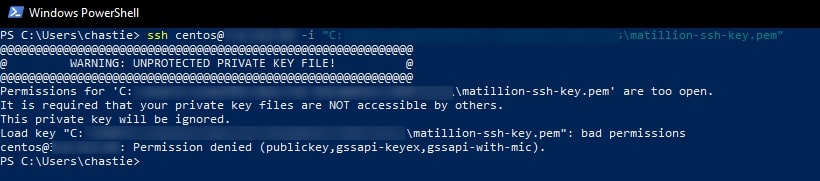
2. To avoid this error, the private key must be stored securely so that only your user is able to access it. We must modify the properties of the private key file so that no other user can access it. Begin by right-clicking on the private key file and opening the properties:
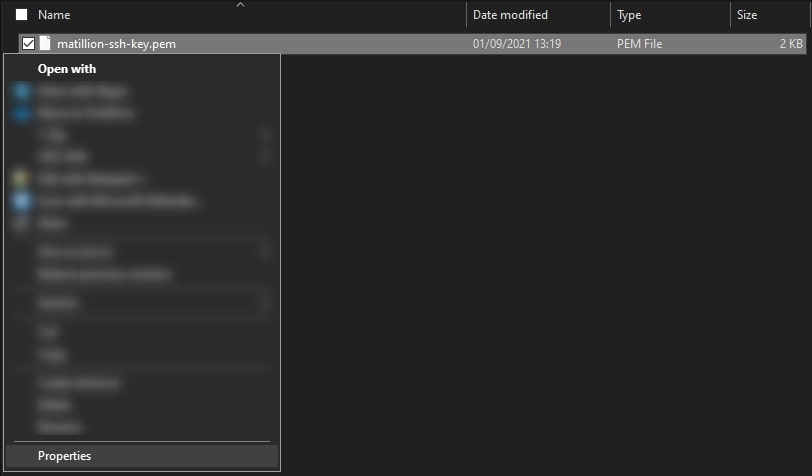
3. On the Security tab, select Advanced:
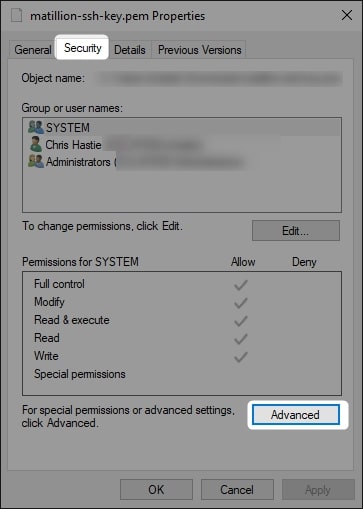
4. If you are not already, change yourself to the owner of the file:
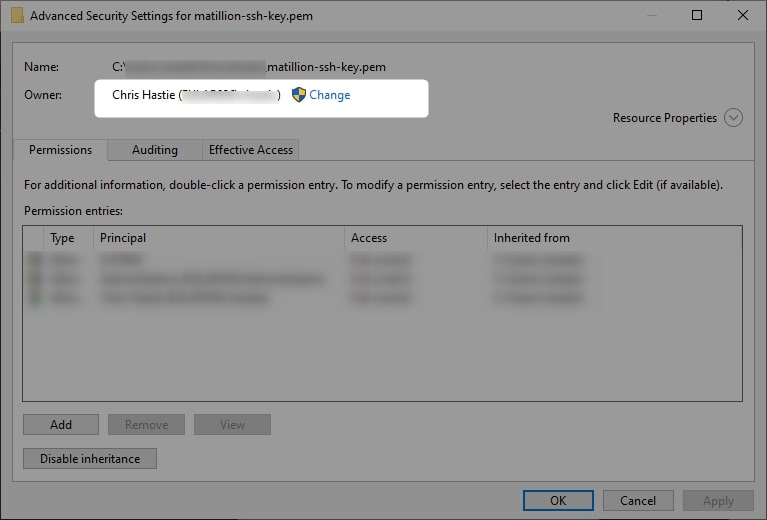
5. Disable the inheritance on the object and remove all inherited permissions:
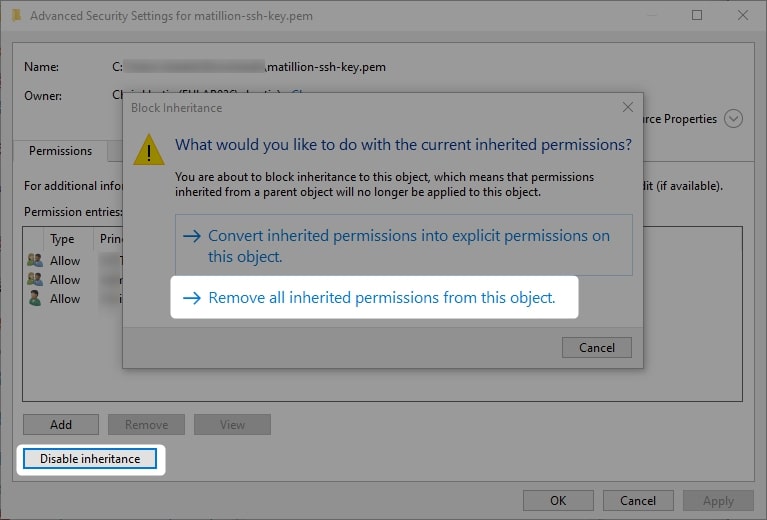
6. Add yourself to the permitted users and grant yourself full control:
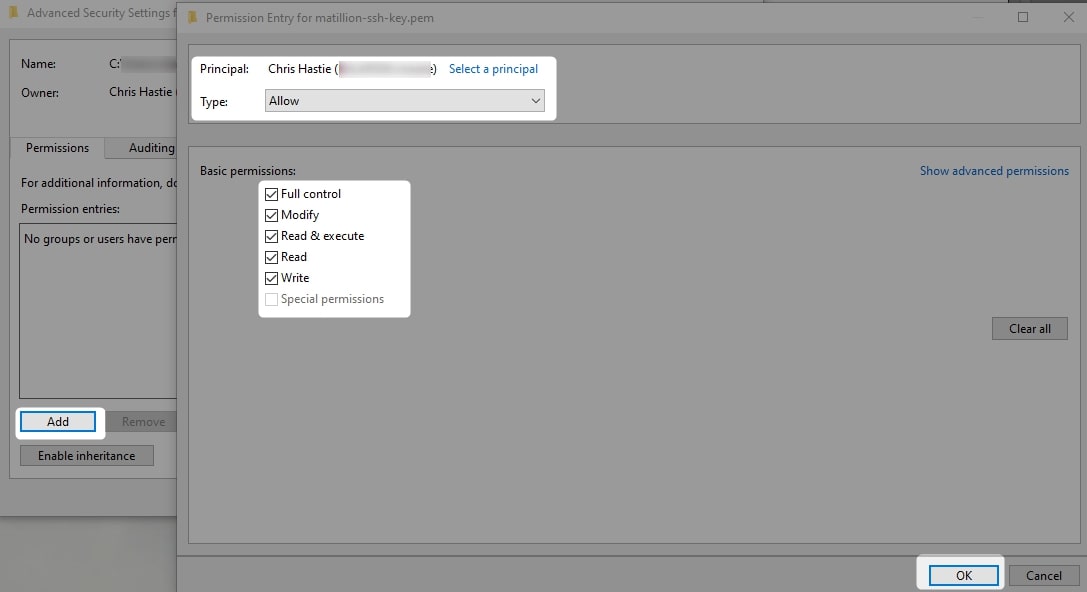
7. Apply the changes and click OK. You should now be able to return to the console and run the same ssh user@host -i path/to/private/key command to access the server:
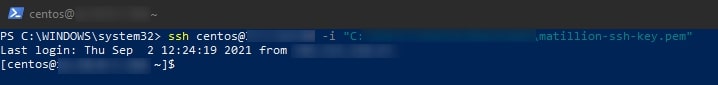
So there were a few more steps involved to set up the appropriate security on the private SSH key, but once you have things set up, you can log in with this same single line of code when needed for a smooth experience.

